Microsoft releases urgent OS patch in wake of #WannaCry ransomware blitz

Microsoft has taken the “highly unusual” step of securing older operating systems in the wake of a massive ransomware attack that wreaked havoc on global computer networks, including the UK’s National Health Service.
Microsoft XP received the new security patch three years after the computer giant discontinued support for the OS.
READ MORE: Ransomware virus plagues 100k computers across 99 countries
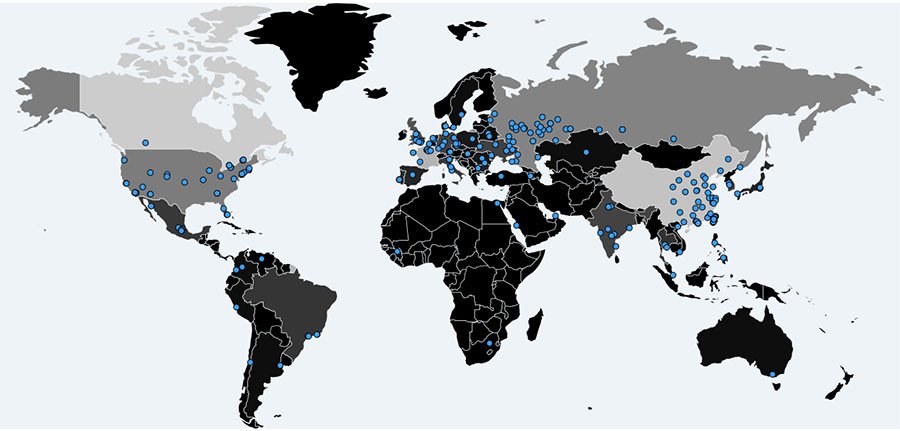
The patch release comes after a virus known as ‘WannaCry,’ ransomware which encrypts files and demands users pay for their release, infected more than 100,000 computers worldwide on Friday.
Malware Tech reports that approximately 124,000 computers have now been affected by the virus, with parts of the UK’s National Health Service, including patient records and other administrative data, debilitated by the sudden attack.
Our statement on the reported ransomware issues: https://t.co/Pt47dvpbiR#nhscyberattack
— NHS Digital (@NHSDigital) May 12, 2017
#wcry#WannaCry#WannaCrypt0r#ransomware hitting 100k Avast detections in less than 24 hours. 57% in Russia. Patch your systems!
— Jakub Kroustek (@JakubKroustek) May 13, 2017
“Seeing businesses and individuals affected by cyberattacks, such as the ones reported today [Friday], was painful,” a Microsoft statement read.
“We are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.”
An investigation is currently underway to determine the source of the cyberattack. According to the European Cybercrime Centre, Europol is “working closely” with countries affected by the blitz to identify the culprits.
NSA exploit codes were released by The Shadow Brokers hacking group earlier this year. The US government cyber weapons were later offered at auction for billions of dollars in bitcoin.
READ MORE: Leaked NSA exploit blamed for global ransomware cyberattack
Earlier this year, Microsoft created a patch called MS17-010 to guard against the virus. But older, unsupported operating systems were not included in the update.
“WannaCrypt’s spreading mechanism is borrowed from well-known public SMB exploits, which armed this regular ransomware with worm-like functionalities, creating an entry vector in machines still unpatched even after the fix had become available,” Microsoft said.
Some analysts are suggesting by sinkholing the domain we stopped the infection? Can anyone confirm?
— MalwareTech (@MalwareTechBlog) May 12, 2017
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.
— MalwareTech (@MalwareTechBlog) May 13, 2017
Elsewhere, a Twitter user posting under the name of @malwaretechblog is being hailed an unlikely hero after they registered a domain name referenced in the virus code. The domain registry acts as a kill switch in the code, halting the ransomware.
Darien Huss, a security research engineer who reportedly helped find the loophole, explained: “WannaCry propagation payload contains previously unregistered domain, execution fails now that domain has been sinkholed.”
#WannaCry propagation payload contains previously unregistered domain, execution fails now that domain has been sinkholed pic.twitter.com/z2ClEnZAD2
— Darien Huss (@darienhuss) May 12, 2017












