Electronic al-Qaeda Army claims to have hacked US government websites
Cyberwarriors in Tunisia and China have reportedly joined forces with al-Qaeda hackers in order to attack United States government websites.
Hackers pledging allegiance to the Tunisian Cyber Army claim to have compromised the security of US State Department and Department of Defense websites as part of an anti-America campaign called Operation Black Summer, or #OpBlackSummer.
The actors taking credit for the breach say they managed to infiltrate government databases to pilfer information along with the help of the al-Qaeda Electronic Army (AQECA) and additionally are working in cooperation with Chinese cybercriminals as part of the operation.
“There are some Chinese hackers who collaborate with us,” a member of the Tunisian Cyber Army tells HackRead.com.
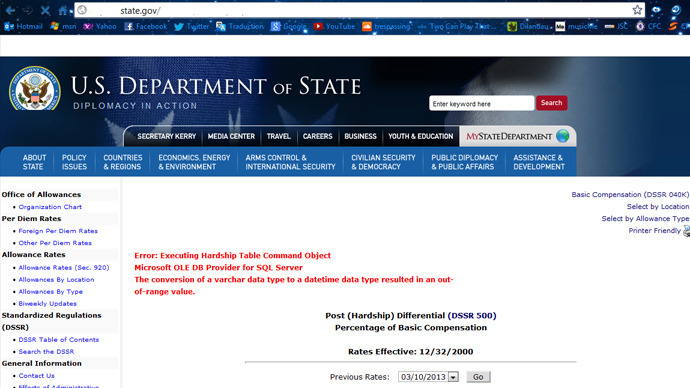
According to the website illsecure.com, the hackers successfully extracted information hosted on at least two US government databases by exploiting SQL injection vulnerabilities on the State Department’s Diplomacy In Action website, as well as the website for the agency’s official State Department magazine.
A SQL injection is one of the most commonly employed techniques used by hackers and involves inputting malicious code into entry fields on website forms in order to wreak havoc.
“SQL databases display a range of data after they've been fed specific statements or queries. So all an attacker needs to do to gain access is pass their malicious query into an unprotected form,” software developer Griffin Boyce tells RT. “Most content management systems have safeguards in place to prevent these kinds of attacks, but custom-coded systems like those created for governments or large businesses tend to be the most vulnerable,” Boyce says. “Which is rather ironic, if you think about it.”
The claims of newly waged assaults on US government websites come on the heels of ramped-up warnings about cyberattacks stemming from foreign agents. US President Barack Obama spent a portion of last month’s State of the Union address condemning foreign cybercriminals and authorized an executive order in an attempt to start curbing the attacks. During a congressional committee hearing last week about the executive order, Sen. Jay Rockefeller (D-WV) said cyberattacks are "the number one national security threat that the country faces."
And although the president has tasked the Department of Homeland Security with designing a framework to protect America’s critical infrastructure from a such an attacks, the wheels have only recently been set into motion to only a fraction of the degree the Obama administration demands. Depending on the severity of the latest hacks, establishing a framework to protect the country might come too little too late.
Speaking with illsecure.com, the Tunisian Cyber Army agents say they have obtained sensitive information from the State Department, as well as the IP addresses of government computers and servers. The Hackers Post adds that their reign of terror didn’t stop there with the Department of State, though. The website says that hackers with both the Tunisian Cyber Army and the AQEA have also breached an official Pentagon subdomain using a similar assault. In that instance, a cross site scripting exploit was launched in order to hack the website for the Army National Guard.
The Hackers Post say the people involved provided a screenshot which shows the execution of vulnerability, and additionally call the exploit an embarrassment for the Department of Defense.
“It’s quite embarrassing that Pentagon website is vulnerable to the most common flaw, which exists in one of its sub domain. This left a question to the Pentagon web security team that such a common [cross site scripting] flaw exists in their server,” writes the website’s Nauman Ashraf.














